
At 3:00 a.m., the cell phone alarm blew up - the server traffic soared to 300 times the usual, and players dropped out like crazy. As a boil bald three technical director of the old gun, I use blood and tears experience summarized this set of The "Golden 30" Emergency Procedure + eradication programThe
I. At the outbreak of an attack: regaining control (0-30 minutes)
1. Rapid diagnosis of the type of attack
- symptomatic → Type of attack → Response tools
! Players transient/lagging en masse → UDP flooding → Enable traffic cleaning
! Login/payment interface paralyzed → CC attack → interface flow restriction + human verification
! Server connection count full → TCP SYN Flood → kernel tuning2. Three tricks to stop the bleeding in an emergency
- Cloud Backend Seconds Cleaning(available on all vendor consoles):
# Simultaneous blocking of TOP10 attacking IP segments (extracted from monitoring logs)
for ip in $(cat attack_ips.txt | head -10); do
iptables -A INPUT -s $ip -j DROP
doneCore Interface Failure
# Flow limiting on login interface in Nginx (1IP/sec)
location /login {
limit_req zone=one burst=5 nodelay;
limit_req_status 429; # return 429 status code
}- Operational downgrades: Turn off real-time voice/world channels and keep the core links for combat and payment.
Deadly Misconceptions::
✘ Blindly rebooting servers (may trigger hacker backdoors)
✘ Manually adjust routing (prone to network-wide paralysis)
II. After a pause in the attack: building a steel barrel defense
1. Protocol layer encryption - making it invisible to hackers
- dynamic key exchange (DKE)(countering protocol forgery):
// StoneCDN SDK example: changing keys every hour
StoneSDK.RotateKey(interval: 3600); - Private Agreement Confusion(CDN5 core technology):
By randomizing the packet characteristics, it makes it impossible for the attacking traffic to identify the protocol structure.
2. System layer hardening - plugging underlying vulnerabilities
# Anti-SYN Flood kernel parameters (mandatory for all Linux servers)
echo "net.ipv4.tcp_syncookies=1" >> /etc/sysctl.conf
echo "net.ipv4.tcp_max_syn_backlog=2048" >> /etc/sysctl.conf
sysctl -p3. Architecture-level protection - business never falls offline
- StoneCDN Solutions::
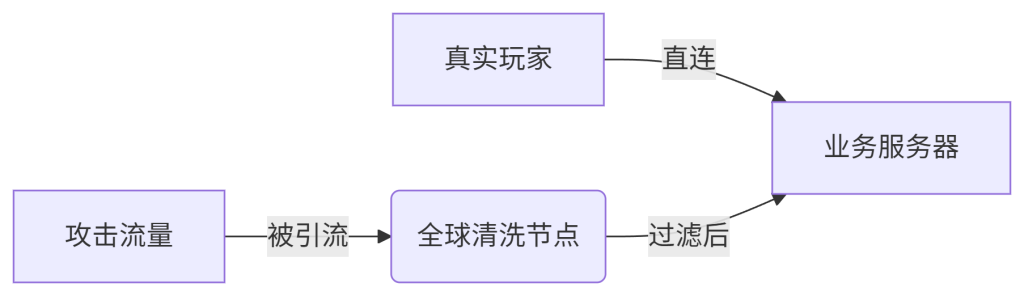
- dominance: $1000 machine frame rate loss <5%, memory footprint 18MB
- be applicable: Small to medium sized games/APP (protection cap 300Gbps)
CDN5 program::
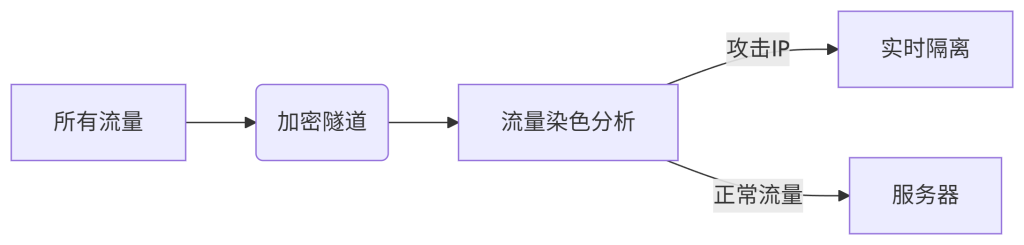
- dominance: Carrying 510Gbps+ Hybrid Attacks
- consideration (in share dealing): deep tuning required (asynchronous loading conflicts need to be fixed manually)
III. Ultimate Defense: Either One or the Other by Business Genetics
Scenario 1: Small and medium-sized teams seek stability and peace of mind → StoneCDN
- Integration speed: Unity plugin imported in 10 minutes, API only 3 functions
- Dynamic degradation: Use light encryption (power-saving 30%) for weak attacks, cut AES-256 for strong attacks
- cost comparison: indicators traditional high defense IPStoneCDN300G protection ¥ 90,000 / month ¥ 4800 / month frame rate impact cleaning delay 200ms + thousand dollar machine 38 → 36fps
Scenario 2: Technical team pursues extreme resistance to beatings → CDN5
- anti-mixing attack::
- 510Gbps UDP flood + 870,000/sec CC attack full blocking
- "One machine, one secret" dynamic key (20 times more expensive for hackers to forge)
- QUIC Acceleration::
Southeast Asian player latency from 186ms → 62ms (retention +14%)